There is danger in any form of communication. Most fraud begins with an email, but messaging apps, social media platforms, gaming platforms, and web pages can also be used to mislead, misinform, or commit crimes. Let’s examine some hidden dangers.
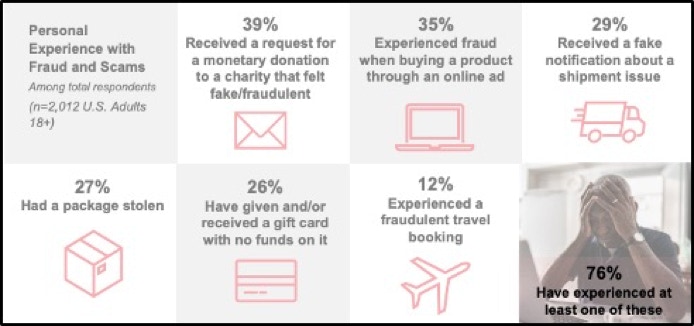
According to a report issued in 2022 by AARP concerning safe shopping practices, the majority (76%) of U.S. consumers have experienced fraud. Figure A-1 shows some statistics from this report.
FIGURE 1. SURVEY RESULTS OF AMERICANS EXPERIENCE WITH FRAUD.
Many websites offer information about scams and fraud. The most comprehensive of these is sponsored by AARP – The American Association of Retired People, a US non-profit organization. The information AARP provides is available to all on the open web, meaning you do not have to register an account to access the descriptions and advice provided.
If you are reading the printed version of this book, you can visit the appropriate page by scanning this QR code. If you have the Kindle version of this book, just click on this link: https://www.aarp.org/money/scams-fraud/, and scroll to near the bottom of the page to the section labeled FRAUD RESOURCE CENTER, where you will find information on about 80 types of scams listed in alphabetical order, from A to Z.
The list below provides very brief definitions of these scams for quick reference. If you see one or more you want to learn more about, visit the link above using your browser. Beyond a more thorough discussion of each scam, supplemental information is provided under the following or similar headings:
• Warning Signs
• How to protect yourself from this scam
• More Resources
AARP also offers a free service called the AARP Fraud Watch Network Helpline which is available toll-free at 877-908-3360. The service is open Monday through Friday, 8 a.m. to 8 p.m. ET.
List of Scams documented on the AARP website:
Apartment Rental Scams Apartment rental scams are deceptive schemes where fraudsters pose as legitimate landlords or property managers to exploit unsuspecting renters. They often advertise attractive rental properties at enticingly low prices, luring potential victims into providing personal information or making upfront payments. These scams can involve fake listings, nonexistent properties, or even hijacked legitimate listings. Victims may be asked to wire money, provide sensitive financial details, or sign fraudulent lease agreements.
Business email compromise (BEC) is a sophisticated cybercrime targeting organizations and their employees. In a BEC scam, fraudsters impersonate company executives, suppliers, or other trusted individuals through email communication. They employ social engineering techniques to deceive employees into divulging sensitive information or conducting fraudulent financial transactions. These scams often involve requests for wire transfers, invoice manipulation, or disclosing confidential data. BEC attacks can be financially devastating for businesses, resulting in substantial financial losses and reputational damage. This scam is discussed in more detail in the following section:
Car Warranty Scams. Car warranty scams are fraudulent schemes that target vehicle owners by offering fake or unnecessary extended warranty coverage. Scammers typically contact individuals via phone, email, or direct mail, posing as representatives from reputable car manufacturers or warranty companies. They use high-pressure tactics, such as urgent deadlines or false claims of expiring warranties, to convince victims to purchase their fraudulent plans. These scams often involve collecting personal and financial information and upfront payments for bogus warranties.
Caregiver Fraud. Caregiver fraud refers to deceptive practices where individuals posing as caregivers exploit vulnerable individuals, such as the elderly or disabled, for financial gain. These fraudsters may be hired through unverified sources or present themselves as trustworthy professionals with false credentials. They commit fraud once they access the victim's home or personal information. This can include stealing valuables, misusing credit cards or bank accounts, forging checks, or manipulating financial documents.
Catfishing Scams. Catfishing scams are deceptive schemes in which individuals create fake online personas to lure unsuspecting victims into romantic relationships or gain their trust for personal gain. Scammers often use social media platforms, dating websites, or online forums to initiate contact with their targets. They may steal photos and personal information from others or create fictional identities to establish a false sense of connection and intimacy. Once trust is established, the catfisher may exploit the victim by requesting money, sharing fraudulent investment opportunities, or extracting sensitive information.
Celebrity Impostor Scams. Celebrity impostor scams involve fraudsters pretending to be famous personalities, such as celebrities or public figures, to deceive unsuspecting individuals for financial gain. These scammers often create fake social media profiles, impersonate celebrities through emails or phone calls, or engage in online interactions claiming to be the celebrity themselves or their representatives. They may promise exclusive opportunities, endorsement deals, or special favors in exchange for money or personal information. Victims of celebrity impostor scams can suffer significant financial losses and have their personal information compromised.
Census Scams. Census activity isn’t limited to years ending in 0, nor is census fraud. Along with its once-a-decade population count, the Census Bureau conducts more than 130 surveys yearly. Census scams are fraudulent activities where individuals or organizations posing as census officials gather sensitive personal information or extract money from unsuspecting individuals. Scammers may reach out to people through phone calls, emails, or door-to-door visits, claiming to be conducting the national census or a survey on behalf of the government. They may request personal details such as social security numbers, bank account information, or credit card details under the guise of data collection. Sometimes, they may even ask for payment for participation in the supposed census.
Charity Scams. Charity scams are deceptive tactics fraudsters employ to exploit people's generosity and goodwill for personal gain. Scammers may pose as representatives of legitimate charitable organizations or create fictitious charities, often using emotional appeals to elicit donations. They may reach out via phone calls, emails, social media, or door-to-door visits, claiming to collect funds for various causes such as disaster relief, medical research, or support for the underprivileged. However, the donations received are rarely used for their intended purpose.
Credit Card Interest Rate Scam. There’s a booming market for scammers peddling phony promises to reduce your credit card rates, slash interest payments and help you pay down big balances. Robocalls, claiming to be from banks or credit card companies, urge you to switch your account to low or no interest immediately. If you bite, a live operator takes over, pumping you for card numbers and other data they can use for identity theft. Other callers say they’re from debt-relief companies with insider know-how in negotiating lower rates with card providers. They’ll charge hefty fees for things you can do yourself, like transfer your balance to a lower-rate card or sign you up for a new card with a limited-time 0 percent APR.
Credit Repair Scams. Credit repair scams are fraudulent schemes that prey on individuals seeking to improve their credit scores and financial standing. Scammers may advertise through online ads, social media platforms, or even cold-calling, promising to remove negative information from credit reports, create a new credit identity, or guarantee a significant increase in credit scores. They often require upfront fees or payments for their services, claiming insider knowledge or secret techniques to fix credit issues quickly. However, these scammers rarely deliver on their promises and may even engage in illegal activities that can further damage the victim's credit.
Cruise Scams. Cruise scams are fraudulent activities that target individuals looking to book or enjoy a cruise vacation. The classic cruise con starts with an email or (often automated) phone call with news that you’ve won a free cruise — as a sweepstakes prize, a special offer from a travel company, or a “reward” for taking a brief survey. Scammers may claim to represent well-known cruise lines or travel agencies, but their primary goal is to extract personal and financial information from unsuspecting individuals. These scams can involve fake tickets, non-existent cruises, or hidden fees revealed after payment. You might be asked to provide a Social Security number to reserve your spot or credit card details to cover nominal booking or processing fees.
Cryptocurrency Fraud. Unlike government-backed money, the value of virtual currencies is driven entirely by supply and demand. That can create wild swings that produce big gains or losses for investors. Investments in cryptocurrencies are subject to far less regulatory protection than traditional financial products like stocks, bonds, and mutual funds. Cryptocurrency fraud encompasses various fraudulent activities aimed at exploiting individuals in cryptocurrencies. Scammers may use techniques such as phishing, Ponzi schemes, fake initial coin offerings (ICOs), or fake cryptocurrency exchanges. They often lure victims with promises of high returns, exclusive investment opportunities, or quick profits in the cryptocurrency market. These scams can involve stolen funds, unauthorized access to digital wallets, or the sale of non-existent cryptocurrencies.
Customer Service Scams. Customer service scams involve fraudulent activities where scammers pose as customer service representatives to deceive individuals and obtain their personal information or money. These scams can occur through phone calls, emails, or fake websites. Scammers may pretend to represent legitimate companies, such as banks, utility providers, or tech support, and create a sense of urgency or concern to manipulate their victims. They may request sensitive information like Social Security numbers, bank account details, or passwords, claiming it is necessary to resolve an issue or provide assistance. Alternatively, they may request payment for bogus fees or services.
Debt Collection Scams. Fake debt collectors use abusive or threatening tactics to collect money that isn't owed. A federal rule change in November 2021 allows collectors to contact debtors by email, text, or social media direct message and phone (previously the only sanctioned method), opening new routes for fake-debt scammers to reach their targets. Occasionally such situations arise from mistaken identity: A legitimate debt collection agency slips up, confusing a consumer with a debtor who has a similar name. Often, though, it’s a scammer, combining bits of personal information harvested from various sources to fabricate bogus debts that consumers might be deceived into thinking are real.
Debt Relief Scams. Debt relief scammers offer sham “guarantees” to get you out of debt quickly and cleanly and ask you to pay them before they do anything for you, which is illegal, according to the Federal Trade Commission (FTC). Even with legitimate companies, debt settlement carries considerable risk. Many firms instruct clients to stop paying their debts because this will compel creditors to negotiate a reduction. It might — but creditors are under no obligation to settle rather than sue; in the meantime, you could accrue interest and penalties and damage your credit score. According to the FTC, some firms don’t fully explain the potential consequences. The commission encourages consumers to weigh various options when looking for ways to dig out debt.
Disaster Scams. Disaster scams are fraudulent activities that exploit people during natural or man-made disasters. Scammers use the vulnerability and urgency of individuals affected by these events, such as hurricanes, earthquakes, or public health crises. They may impersonate charitable organizations, government agencies, or relief workers, using various communication channels to deceive victims. These scams can involve requests for donations, offers of fraudulent services, or the sale of counterfeit products claiming to help with recovery efforts.
DMV Scams. DMV scams are a form of phishing that takes advantage of government offices’ efforts to provide more services online, including driver’s license renewal in many states. Crooks seek to lure motorists to phony versions of government websites on the pretext of helping them with tasks such as license renewal or title transfer.
Scammers send emails designed to look like they come from the state motor vehicle agency, complete with logos or copied content, warning that you need to update your personal information to keep your license or that you have an unpaid ticket. Even if you don’t provide any data, clicking a link in the message could infect your device with malware.
Some criminal operations skip the texts and emails and go straight to the bogus website. They register URLs that contain state names and terms like “license,” “registration,” or “DMV” and rely on search engines to serve up the sites to consumers looking online for driver information.
Email Extortion Scams. Email extortion scams threaten to publicize compromising information about you — true or not — if you don’t make a quick payment. Extortion scammers have a valuable scare tactic: They show in their messages that they know a password you’ve used for online accounts. They claim they’ve implanted malware on your computer that lets them capture your keystrokes, watch through your webcam, and amass evidence that you, say, frequent adult websites. And they say they’ll share that information with all your email and social media contacts — perhaps with a video of you enjoying your viewing — unless you pay hush money. Extortion scammers send out threats indiscriminately, using big batches of email addresses and associated passwords that they likely obtained on the black market following big corporate data breaches. They hope to stumble across a few people who don’t change their passwords regularly or have some secret they don’t want others to know. That there have been actual cases of hackers gaining access to people’s webcams gives the scam a veneer of plausibility.
Fake Check Scams. Fake check scams involve fraudulent activities where scammers send counterfeit checks to unsuspecting individuals, often as part of a larger scheme. These scams can take various forms, such as fake lottery winnings, job opportunities, or online sales transactions. The scammers typically instruct the victim to deposit the check and then return a portion of the funds to them or a third party. However, the deposited check is counterfeit, and by the time it bounces, the victim has already sent money to the scammer. This leaves the victim responsible for the funds and potential legal consequences.
Free Trial Scams. These scams entice you with offers that pop up on social media sites or rank high in search results, thanks to paid ads. They might tout no-risk trials of things such as magazines or streaming services. However, thanks to a scientific advance or miracle ingredient, most focus on personal care, promising whiter teeth, fewer wrinkles, or rapid weight loss. Some free-trial offers are “subscription traps” designed to deceive you into signing up for regular deliveries of questionable products.
Funeral Scams. In planning and paying for a final farewell, it’s important to think clearly and be wary: Some unscrupulous operators take advantage of families’ most trying times for their monetary gain. Unethical funeral directors seek to collect thousands more by overcharging for items or tricking you into buying packages with extra features you don’t want or need.
Gift Card Scams. Contacting you in the guise of someone else — often a representative of a government agency, such as the IRS or Social Security Administration, or a well-known company — scammers claim you owe a debt or need a service. They insist you buy gift cards and read them the serial and personal identification number (PIN) on the back to make quick payments. Genuine businesses and government bodies never ask for payment via gift card. Any such request is a sure sign of fraud.
Government Grant Scams. Government grant scams involve fraudulent activities where scammers pose as representatives of government agencies, offering individuals the opportunity to obtain free grants or financial assistance. These scammers typically reach out through unsolicited phone calls, emails, or social media messages, claiming the individual has been selected for a government grant. They may request payment for processing fees, personal information, or bank account details under the guise of facilitating the grant disbursement. There is no legitimate grant, and scammers aim to deceive victims into providing money or sensitive information for their financial gain.
Grandparent Scam. The grandparent scam is a common telephone scam targeting older individuals. Scammers pose as a grandchild or another distressed family member and urgently request money. They often claim to be involved in an accident, arrested, or facing other emergencies. The scammer manipulates the victim's emotions and requests immediate financial assistance, typically via wire transfer or gift cards. By exploiting the grandparent's love and concern, scammers attempt to deceive them into sending money before they realize it's a fraud. Voice cloning, facilitated by AI tools, can make the grandparent scam more convincing and effective. By utilizing voice synthesis technology, scammers can replicate the voice of a grandchild or family member with remarkable accuracy. This allows them to sound exactly like the person they claim to be, enhancing their credibility and tricking the targeted grandparent.
Greeting Card Scams. Greeting card scams involve deceptive practices where scammers send fraudulent greeting cards or e-cards to unsuspecting individuals, often with malicious intent. These scams can take various forms, such as e-cards containing malware or links to malicious websites or physical cards requesting personal information or payments. These scams aim to trick recipients into compromising their private information or falling victim to financial fraud. Not surprisingly, they proliferate around occasions when card exchanges are popular: Valentine’s Day, Mother’s Day, and the holiday season.
Health Fraud. The Federal Food and Drug Administration (FDA) defines health fraud as the deceptive advertising, promotion, or sale of unproven products claimed to be effective in preventing or treating a condition or illness. These scams can take various forms and often rely on testimonials, pseudoscience, or false claims of medical expertise to deceive consumers. These scams can jeopardize individuals' health, delay medical treatment, or lead to financial losses.
Health Insurance Scams. Health insurance scams involve fraudulent activities that target individuals seeking affordable and comprehensive health insurance coverage. Scammers exploit the complexity of the healthcare system and individuals' need for reliable insurance by offering fake or inadequate health insurance plans. They may use tactics, such as unsolicited phone calls, emails, or online advertisements, claiming to represent legitimate insurance companies or government programs. These scams can involve promises of low premiums, minimal deductibles, or coverage for pre-existing conditions, enticing individuals to provide personal and financial information or make upfront payments. However, the scammers have no intention of giving legitimate insurance coverage and often disappear after collecting payments. During ACA enrollment, scammers impersonate representatives of the government-run health insurance marketplace. They’ll tell you they need personal information to verify an application or that they can help you choose the right plan — for a fee.
Holiday Scams. Three-quarters of U.S. consumers have experienced or been targeted by at least one form of fraud that can be tied to the holidays, including requests from (often fake) charities, online shopping scams, and fraudulent communications about shipping problems, according to a recent AARP Fraud Watch Network™ report, “Preparing for the Holidays? So Are Criminals: Already Rampant Fraud Expected to Spike.”
Most scams are variations of everyday fraud, ramped up to match seasonal spikes in spending and web traffic. Not surprisingly, they often center on shopping, especially online. As real retailers roll out their seasonal deals, scammers seek to snare bargain-hunting shoppers with bogus websites and social media campaigns that impersonate major brands. These “spoofing” sites and fake posts entice you to spend money on products you’ll never receive.
Many are vehicles for harvesting credit card numbers and other personal data that criminals use to commit identity theft or sell on the dark web. Scammers may distribute malware-loaded links or attachments via supposed coupon offers or “order confirmation” emails. Fraud involving drained gift cards — hugely popular for giving and receiving — also shifted into high gear.
Home Improvement Scams. If you are a homeowner, it’s not uncommon to have contractors show up on your doorstep uninvited. They say they happened to be doing some work in the neighborhood and noticed that your house needs some repairs, too. They offer to fix your roof, repave your driveway, or perform other repairs or renovations, for what sounds like a great price. The smiling fix-it man or woman at your door might turn out to be an unscrupulous contractor or an outright con artist out to fleece you with a home improvement scam.
Home improvement scammers will often ask for payment upfront. Some disappear with your money. Others will do shoddy work or claim to have discovered some hidden problem in your house that needs immediate attention and significantly raises the cost (a dishonest variation of the sales tactic known as upselling).
Crooked contractors look to prey on people they view as vulnerable. If your house has been damaged by a storm or natural disaster, for example, a scammer might show up and promise fast, cheap repairs or persuade you to sign over a payment from your insurance company.
Identity Theft. Identity theft occurs when someone obtains someone else’s personal information, such as a Social Security number, home address, date of birth, or bank account data, and uses it for fraud or other illicit purposes.
Credit-reporting agency Experian lists 16 distinct types. (Some, such as tax ID theft and Social Security number scams, are discussed in greater detail elsewhere in the Fraud Resource Center.)
Identity thieves swarm the internet and often target older Americans, who tend to be slow to adopt new fraud-prevention technologies and are loath to change their online habits even when they've experienced fraud, according to an October 2020 study produced by digital finance consulting firm Javelin Strategy and Research and sponsored by AARP.
These scammers have a range of tactics to get what they need, from the old school (stealing your mail) to high-tech (massive hacks of banks, retail chains, and other companies that stockpile consumer data). They might pretend to be from utilities, banks, or big tech firms to get their hands on identifying information or send phishing emails with links that infect your device with data-harvesting malware.
Most often, they claim to represent government agencies, soliciting personal or financial data on the pretext of helping you collect benefits or navigate the bureaucracy. This tactic exploded during the COVID-19 pandemic as criminals exploited the distribution of trillions of dollars in federal relief funds.
Impostor Scams. Impostor scams involve fraudulent activities where scammers pretend to be someone they are not to deceive individuals and gain their trust. These scams can take various forms, such as impersonating a trusted professional, a company representative, a government official, or even a family member or friend. This is the most common form of fraud reported to the Federal Trade Commission (FTC).
Impostor scams start with unsolicited phone calls, emails, texts, or social media messages. Fraudsters impersonate people and organizations you would ordinarily trust or at least hear out. The most common pose, accounting for 40 percent of impostor reports to the FTC, involves government agencies such as Social Security, Medicare, or the IRS. But crooks might adopt any number of guises.
Investment Fraud. Investment fraud involves deceptive practices where scammers target individuals seeking investment opportunities to defraud them of their money. These scams can take various forms, such as Ponzi schemes, pyramid schemes, or fraudulent investment schemes promising high returns with little to no risk. Scammers often use persuasive tactics, false claims, or fake credentials to gain the trust of their victims. They may offer exclusive investment opportunities, pressure individuals into making quick decisions, or promise guaranteed profits.
Jury Duty Scams. Getting called for jury service is a routine fact of life for most Americans. But if that summons to civic duty comes in the form of a phone call or email, be suspicious: It’s probably a jury duty scam.
Real summonses for jury duty and notices that you’ve skipped it comes in the mail. No court official will demand payment or personal information from you over the phone. And if you genuinely have missed jury duty, no fine will be imposed until you can appear in court to explain your failure to appear.
Medical Equipment Scams. In a medical equipment scam, someone reaches out to you with an offer of a “free” (as in, “Medicare will pay for it”) brace, wheelchair, or other device. You might get an unsolicited phone call, see an advertisement, or be approached at a health fair or similar event.
These scams can include selling counterfeit or substandard medical equipment, such as mobility aids, hearing aids, or home healthcare devices. Scammers may use various tactics, including online advertisements, unsolicited phone calls, or emails, to lure victims into purchasing fake or ineffective products at inflated prices. To deceive individuals, they may falsely claim the equipment's quality, effectiveness, or certification.
Medical Identity Theft. Medical identity theft is the fraudulent use of someone's personal information, such as their name, insurance details, or Social Security number, to obtain medical services, prescription drugs or commit healthcare-related fraud. Scammers may use stolen information to impersonate the victim, seek medical treatment, file false insurance claims, or obtain prescription medications. This can result in medical errors, incorrect medical records, financial loss, and potential harm to the victim's health. But it’s often a matter of “friendly fraud”: Surveys have suggested that nearly half of the victims said their medical ID was used by a relative or someone else they knew.
Medicare Card Scams. Medicare card scams involve fraudulent activities that target individuals enrolled in the Medicare program, particularly seniors. Scammers attempt to exploit the sensitive information on Medicare cards, such as the beneficiary's Medicare number, to commit identity theft or fraudulent billing. They may contact individuals via phone calls, emails, or in-person encounters, posing as Medicare representatives or healthcare providers. They often deceive victims by claiming they need to update their Medicare card information, charging a fee for a new card, or offering unnecessary medical services or equipment.
Medicare Fraud. Medicare fraud involves deliberate and deceptive activities where scammers or healthcare providers unlawfully bill the Medicare program for services or supplies that were either not provided, unnecessary, or at inflated prices. These fraudulent practices can result in significant financial losses for the Medicare program and harm beneficiaries by leading to inappropriate medical treatments or denying them necessary care. Scammers may engage in various forms of Medicare fraud, such as submitting false claims, using stolen Medicare numbers, or participating in kickback schemes.
Money Mule Scams. Money mule scams involve individuals scammers recruit to transfer stolen funds or engage in illegal money laundering activities. Scammers target vulnerable individuals, often through job postings or online advertisements, offering lucrative work-from-home opportunities or promising easy money. Once recruited, the victims are instructed to receive money into their bank accounts and then transfer it to another account or convert it into cryptocurrency, keeping a portion of the funds as their commission. However, the money being transferred is typically obtained through illegal activities such as phishing, identity theft, or other forms of fraud. By involving innocent individuals as intermediaries, scammers aim to obscure the trail of unlawful transactions, making it harder for law enforcement to track illicit funds.
Mortgage Relief Scams. Mortgage relief scams are fraudulent activities that prey on homeowners facing financial difficulties or struggling to make mortgage payments. Scammers take advantage of these vulnerable individuals by offering false promises of assistance in obtaining mortgage modifications, refinancing, or foreclosure prevention. They often target homeowners through phone calls, emails, or even door-to-door visits, claiming to be from legitimate organizations or government agencies. These scammers may request upfront fees, collect personal and financial information, or mislead homeowners into signing documents that transfer the ownership of their homes. Ultimately, the scammers fail to deliver their promises, leaving homeowners in even worse financial situations.
Moving Scams. Moving scams involve deceptive practices by unscrupulous moving companies to exploit individuals relocating their belongings. These scams can take various forms, such as holding belongings hostage, providing lowball estimates, demanding unexpected additional charges, or even disappearing with the belongings altogether. Scammers often prey on individuals under time constraints or seeking inexpensive moving services. They may advertise attractive rates or offer unrealistic discounts to lure customers in, only to engage in fraudulent activities during moving.
Nigerian Scams. One of the first cons to flourish on the internet, the “Nigerian prince” scam, also known as the “419” scam (named for the section of Nigeria’s criminal code dealing with fraud), has an ignominious history that long predates the digital age. These scams typically involve individuals or groups who attempt to defraud victims by enticing them with the promise of a large sum of money in exchange for upfront fees or personal information. The scammers often pose as wealthy individuals, government officials, or representatives of organizations in distress. They may reach out through emails, social media messages, or even phone calls, using various tactics to gain the trust of their victims. Common Nigerian scams include lottery, inheritance, and business investment scams.
Obituary Scams. These scams involve malicious individuals who scour obituaries or funeral announcements to identify grieving families as potential targets. They may pose as compassionate individuals offering condolences or services such as writing obituaries, organizing memorial events, or handling financial matters related to the deceased. However, they intend to exploit the grieving family for financial gain. These scams can involve identity theft, fraudulent invoicing, or the misappropriation of funds for funeral expenses or estate settlements.
Online Banking Scams. These scams start with an email or text that appears to come from a real financial institution, down to an authentic-looking logo. These spoofed communications carry urgent but phony warnings about problems with an account or transaction.
You might be directed to call a supposed customer service line (where you'll be pressed for personal information like a Social Security number) or to click on a link that takes you to a fake banking website. That could be a trap to infect your device with malware that allows crooks to track your keystrokes and capture account credentials.
Signs of phishing can include misspellings and poor grammar; email or web addresses that resemble but don't quite match the real domain (look for a switched letter or extra punctuation mark); or generic greetings like “Dear Valued Customer."
Online Pharmacy Scams. Online pharmacy scams are deceptive schemes that exploit the growing popularity of online pharmacies. These scams typically involve fraudulent websites or individuals posing as legitimate pharmacies, enticing unsuspecting customers with discounted prescription or over-the-counter drug prices. Once customers place orders and provide their personal and financial information, scammers send counterfeit or substandard medications or vanish without fulfilling the orders. These scams can have serious consequences for victims, including health risks from consuming fake or ineffective drugs, financial loss, and compromised personal information. To protect oneself, it is crucial to exercise caution, verify the legitimacy of online pharmacies, and consult with healthcare professionals before making any purchases.
Online Shopping Scams. Online shopping scams exploit the convenience and popularity of e-commerce platforms to deceive and defraud unsuspecting shoppers. Scammers create fake online stores or listings on legitimate platforms, offering attractive deals on popular products or hard-to-find items. They may use stolen product images and descriptions to make their listings appear genuine. Victims are enticed to make purchases and provide payment, but they either receive counterfeit or inferior products or nothing. Scammers may also collect personal and financial information during the transaction, leading to identity theft or unauthorized charges. To protect yourself from online shopping scams, it is crucial to research the legitimacy of the seller or online store, read reviews and ratings from other customers, ensure the website has secure payment options, be cautious of excessively low prices or unrealistic deals, and use reputable and well-known e-commerce platforms. Additionally, it is advisable to review the seller's return and refund policies, keep records of transactions, and promptly report any suspicious or fraudulent activity to the relevant authorities or the platform where the purchase was made.
Package Scams. Package scams involve fraudulent schemes that exploit the delivery of packages to deceive and defraud individuals. Scammers may employ various tactics, such as posing as legitimate shipping companies, offering fake delivery notifications, or creating counterfeit tracking numbers. They may send phishing emails or texts requesting personal information or payment for supposed delivery charges or customs fees. Scammers sometimes may even send empty or low-value packages to establish legitimacy before attempting a more significant scam. These scams can result in financial loss, identity theft, or the compromise of personal information.
Pet Scams. Pet scams exploit people's love for animals by posing as legitimate pet sellers and tricking individuals into paying for pets that don't exist or will never be delivered. Scammers typically advertise popular and desirable breeds of pets at low prices, often accompanied by heartwarming stories. They communicate through online platforms or classified ads and request payment upfront for the pet, transportation, or other related fees. Once the payment is made, the scammers may ask for additional charges, such as insurance or quarantine fees, before disappearing entirely. Victims are left devastated and without the promised pet.
Phishing. Phishing scams aim to acquire valuable personal and financial data, such as your Social Security number, credit card details, or passwords for online accounts, to steal your identity, money, or both. They are mostly associated with email but can come in many forms, including social media messages, pop-up ads, “vishing” (voice phishing by phone), “smishing” (phishing by text message), and “pharming” (drawing victims to bogus websites).
The scam often relies on impersonation, and phishers can be very good at it. They sound authoritative on the phone, trick caller IDs into showing a real corporate or government number, and use well-known logos to make their emails and websites look genuine.
You might even get a phishing email that appears to come from a family member, friend, or work colleague. Some scammers hack accounts and gather personal details on victims to launch highly targeted attacks, a practice called spear-phishing. Global crime gangs use phishing emails in widespread business swindles to penetrate companies’ computer networks or trick employees into paying phony invoices.
Wherever their apparent source, phishing messages feign urgency (act now, or you’ll risk arrest/have your account frozen/miss out on this special offer). You’ll be asked to quickly provide or “confirm” key pieces of personal or business information or be directed to click on a link, which might launch malware that harvests data from your computer or ransomware that takes over the machine and locks you out.
Phone Scams. Phone scammers use false promises, aggressive sales pitches, and phony threats to pry loose information they can use to steal your money or identity. With auto-dialers, shady operators can blast out robocalls by the millions for just a few dollars daily. Nearly 3 in 5 respondents to the Truecaller survey reported receiving a pandemic-related scam call or text message.
Political Scams Political scams exploit the trust and engagement of individuals in the political process for personal gain or deceptive motives. Scammers may pose as political candidates, representatives, or organizations to solicit donations, spread false information, or manipulate public opinion. They often employ phishing emails, robocalls, or fake social media accounts to deceive recipients into providing personal information or contributing funds to fraudulent campaigns. Political scams can also involve voter suppression tactics, such as spreading misinformation about voting procedures or creating fake voter registration drives. These scams undermine the integrity of democratic processes and manipulate individuals' beliefs and actions for the benefit of the perpetrators. It is essential to verify the authenticity of political communications, donate directly to reputable campaigns or organizations, and rely on trusted sources of information to protect oneself from falling victim to political scams.
Ponzi and Pyramid Schemes. Ponzi and pyramid schemes are fraudulent investment scams that promise high returns with little risk. In a Ponzi scheme, the fraudster lures investors by offering abnormally high profits and uses funds from new investors to pay returns to earlier investors, creating an illusion of success. On the other hand, pyramid schemes rely on recruiting participants who are required to make payments or investments. They are incentivized to recruit more individuals who also contribute funds, with the promise of receiving a share of the subsequent investments. Both schemes eventually collapse when there aren't enough new investors to sustain the payouts, leading to significant financial losses for most participants. These scams rely on continuous recruitment and a lack of transparency, often targeting friends, family, or members of a specific community. It is crucial to exercise caution, conduct thorough research, and consult financial professionals before investing in any opportunity to avoid falling victim to Ponzi or pyramid schemes.
Psychic Scams. Psychic scams prey on individuals seeking guidance, reassurance, or closure by exploiting their vulnerability and belief in supernatural abilities. Scammers posing as psychics, clairvoyants, or spiritual advisors promise insights into the future, solutions to personal problems, or connections with deceased loved ones. They often employ techniques like cold reading, vague statements, and leading questions to make general claims seem personalized and accurate. These scams can occur through online platforms, phone consultations, or in-person sessions. Victims are coerced into paying exorbitant fees for additional services, cursed item removals, or promises of good fortune. It is important to approach psychic claims skeptically, scrutinize any requests for money, and prioritize critical thinking over emotional vulnerability to avoid falling victim to these deceptive schemes.
Public Wi-Fi Scams. 4 in 5 U.S. respondents said they use free public Wi-Fi at least occasionally. A third preferred it to using their mobile data service when out and about. Many public networks lack strong security protections, which makes it easy for scammers to break into them.
One common trick is the “evil twin” hack: A scammer sets up a Wi-Fi network with a name similar to the one you expect to use, hoping you’ll connect to it. Another ploy is to launch a “man in the middle” attack, where the hacker takes up a position between you and the Wi-Fi access point you’re trying to use to intercept your data. Once they get in, hackers aim to steal passwords and credit card information or scan emails for sensitive personal data.
OR Code Scams. QR scams involve using Quick Response (QR) codes to deceive and defraud unsuspecting individuals. Scammers create malicious QR codes and distribute them through various channels like email, social media, or physical signage. These codes are often designed to redirect users to fake websites, download malware-infected apps, or prompt unauthorized financial transactions. Once scanned, victims may unknowingly provide sensitive information or grant access to their devices. QR scams have become increasingly prevalent due to the widespread adoption of QR codes for contactless payments and other convenient applications. Therefore, it is crucial to exercise caution when scanning QR codes, verifying their legitimacy, and ensuring the security of personal information.
Ransomware. Ransomware is a particularly devious type of malicious software (called malware). You can inadvertently download ransomware onto your computer or device by clicking on an online ad or email link, opening an attachment, or, in some cases, simply going to a website where it has been planted (a form of attack called a drive-by download).
Once the program installs itself, it will lock up your computer and communicate the demand for payment, usually in cryptocurrency. More vicious strains of malware will encrypt the files and folders on your machine, external drives you have plugged into it, and other computers on your home or office network.
Reverse Mortgage Scams. These scams target older homeowners, offering them false promises of financial security in their retirement years. These scams exploit the complexity of reverse mortgages, presenting them as a solution to various financial concerns. Fraudsters collaborate with mortgage brokers, appraisers, attorneys, and loan officers to deceive homeowners into taking out reverse mortgages. They manipulate property appraisals to inflate equity and convince homeowners to proceed with the loan. Scammers may also use reverse mortgages to promote fraudulent investments, home improvement projects, or as a means to avoid foreclosure. In some cases, they employ property flipping schemes, tricking victims into purchasing rundown houses using reverse mortgages, only to leave them with worthless properties while pocketing the loan funds.
Robocalls. Robocalls continue to plague Americans, approximately 42 percent of which were estimated to be scams. These illegal robocalls range from telemarketing spam to attempts at stealing personal information or money. Scammers employ tactics such as caller ID spoofing to deceive recipients into thinking the calls are from legitimate sources. They pose as utility companies, well-known brands, or government agencies like Social Security or the IRS. Popular scams involve fake offers of free travel, demanding payments for non-existent debts, or enticing victims with prizes or financial opportunities. Engaging with these calls can lead to further harassment or attempts at extracting sensitive data. While some robocalls are legal for informational or noncommercial purposes, it is crucial to stay vigilant against the prevalent threat of automated scams.
Romance Scams. Romance scams are deceptive schemes where fraudsters create fake online profiles and develop emotional relationships with individuals on dating websites or social media platforms. The scammers use manipulation and emotional manipulation to gain the trust and affection of their victims, with the ultimate goal of extorting money or personal information. They often exploit the victim's desire for companionship, love, or intimacy. The scammers may engage in lengthy conversations, express strong emotions quickly, and create elaborate stories to elicit sympathy and trust. Once they have established a connection, they may request money for various reasons, such as medical emergencies, travel expenses, or investments.
The older the target, the heavier the financial toll. According to the FTC, the median individual loss from a romance scam for people 70 and over was $9,000 in 2021, compared to $2,400 across all age groups.
Secret Shopper Scams. Secret shopper scams involve individuals lured into fraudulent schemes claiming to offer lucrative job opportunities as secret shoppers. Scammers often pose as legitimate companies and target individuals seeking flexible part-time work or extra income. They may approach potential victims through email, online job portals, or unsolicited mail. The scammers typically request personal information, such as bank account details, and may send counterfeit checks or money orders for the victims to deposit. Victims are then instructed to evaluate the quality of certain products or services by making purchases and wiring some funds back to the scammers. However, the checks or money orders are fake, and victims lose their money when the bank discovers the fraudulent transaction.
Small Business Scams. Small business scams are fraudulent activities targeting small businesses, often intending to deceive them of money, sensitive information, or valuable resources. Scammers may employ various tactics to exploit the vulnerabilities of small companies, such as impersonating government agencies, offering fake business services, or posing as potential customers or partners. Common small business scams include fake invoicing, directory listing scams, deceptive advertising offers, and phony grant or loan schemes.
Smishing. Smishing scams are fraudulent through SMS (Short Message Service), text messages, or other platforms. The word “smishing” comes from combining “SMS” — for short message service, the technology behind texting — with “phishing,” the practice of stealing personal or financial information through deceptive communications, primarily emails. It's phishing by another means, namely text messages on mobile devices.
Scammers use text messages to trick individuals into revealing personal information, downloading malicious software, or clicking on harmful links. These messages often appear from trusted sources, such as financial institutions, government agencies, or well-known companies, creating a sense of urgency or fear to prompt victims to take immediate action. Smishing scams may involve requests for sensitive information like account numbers, passwords, or social security numbers, or they may direct recipients to fraudulent websites or mobile apps designed to collect personal information or install malware on their devices.
Social Media Scams. Social media scams involve fraudulent activities on popular social media platforms like Facebook, Instagram, Twitter, or LinkedIn. Scammers exploit these platforms' wide reach and interconnectedness to deceive users and manipulate their trust for personal gain. Common social media scams include fake giveaways, phishing attempts, romance scams, impersonation of public figures or brands, and fraudulent investment schemes. Scammers may create fake profiles or hijack legitimate accounts to engage with unsuspecting users. They may use enticing offers, emotional appeals, or deceptive tactics to trick individuals into sharing personal information, clicking on malicious links, making financial transactions, or spreading the scam to their connections.
Social Security Scams. Social Security numbers are the skeleton key to identity theft. And what better way to get someone’s Social Security number than by pretending to be from Social Security? Scammers may contact victims through phone calls, emails, texts, or even in-person encounters, impersonating government officials or Social Security Administration (SSA) representatives. They often create a sense of urgency or fear, claiming that the victim's Social Security number has been compromised, suspended, or involved in illegal activities. The scammers may request immediate payment or threaten legal consequences if personal information is not provided.
Spear-Phishing. Spear phishing is a targeted form involving personalized and highly tailored fraudulent communications aimed at specific individuals or organizations. Scammers gather information about their targets from various sources, such as social media, professional networks, or data breaches, to make their phishing attempts more convincing and credible. Spear phishing messages may appear to come from trusted contacts or reputable organizations, using familiar language, logos, or personal details to deceive the recipient. These scams often employ sophisticated techniques to manipulate individuals into disclosing sensitive information, downloading malware, or performing unauthorized actions. One identified variation targets homeowners: An email supposedly from your mortgage company says your loan has been sold and provides a link to the new lender’s website. Any payments you make there go into the crooks’ pockets.
Student Loan Scams. As of mid-2022, about 43 million people, including 8.9 million age 50 and older, had outstanding federal student loans, with the average debt burden topping $37,600, according to data from the U.S. Department of Education’s Federal Student Aid Office (FSA).
Student loan scams are deceptive practices targeting individuals seeking financial assistance for their education. Scammers prey on the vulnerabilities of students and graduates by offering fake loan forgiveness programs, loan consolidation services, or scholarship opportunities. They often use aggressive marketing tactics, unsolicited phone calls, or misleading advertisements to lure victims into their schemes. These scams may involve upfront fees, promises of unrealistically low-interest rates, or requests for personal information such as Social Security numbers or bank account details.
Survey Scams. Survey scams involve fraudulent activities disguised as legitimate surveys or market research studies. Scammers use various methods to deceive individuals into participating in these surveys to obtain personal information and financial details or engage in other fraudulent activities. They may approach potential victims through email, social media, or online advertisements, promising rewards or incentives for completing the survey. However, these scams are designed to extract valuable information or trick individuals into paying for supposed survey-related expenses.
Sweepstakes and Lottery Scams. Sweepstakes and lottery scams are fraudulent schemes that trick individuals into believing they have won a large sum of money or a valuable prize. Scammers typically contact victims through phone calls, emails, or texts, claiming they have won a lottery or sweepstakes they never entered. They may use official-sounding names or logos to create an illusion of authenticity. To claim the prize, victims must often pay taxes, processing fees or provide personal information. However, in reality, there is no prize, and the scammers are attempting to extract money or sensitive information for their gain.
Tax ID Theft. Tax identity theft occurs when scammers use stolen personal information, such as Social Security numbers, to file fraudulent tax returns and claim refunds on behalf of the victims. This identity theft typically occurs during tax season but can happen anytime. Scammers obtain personal information through various means, including data breaches, phishing attempts, or even stealing physical documents. They then use this information to file fake tax returns, often claiming inflated deductions or credits to maximize the refund. Victims may be unaware of the theft until they attempt to file their legitimate tax returns and discover that one has already been filed using their identity.
Tax Preparation Scams. Tax preparation scams involve fraudulent practices by individuals or companies that offer tax preparation services. These scammers often target taxpayers during tax season, promising inflated refunds, lower tax liabilities, or deceptive schemes to evade taxes. They may advertise their services through unsolicited emails, phone calls, or online advertisements, claiming to be experts in tax preparation or offering special deals. However, they intend to defraud taxpayers by charging exorbitant fees for their services, filing inaccurate or fraudulent tax returns, or engaging in identity theft.
Tech Support Scams. Tech support scams involve fraudsters posing as technical support representatives to deceive individuals into believing their computer or device has a problem. These scammers may use various methods, such as unsolicited phone calls, pop-up ads, or fake websites, to make victims believe they are experiencing a technical issue that requires immediate assistance. They may request remote access to the victim's device, charge fees for unnecessary repairs or software, or steal sensitive information.
Time-Share Resale Scam. Timeshare resale scams involve fraudulent schemes targeting individuals who own timeshare properties and wish to sell them. Scammers typically contact timeshare owners through unsolicited phone calls, emails, or advertisements, claiming to have buyers interested in purchasing their timeshares at lucrative prices. They may promise a quick and effortless sale, requesting upfront fees for listing services, appraisal, or closing costs. However, these scammers have no intention or ability to sell the timeshares and only seek to defraud the owners of their money.
Travel Scams. Travel scams involve deceptive practices aimed at defrauding individuals seeking travel arrangements, such as booking flights, accommodations, or vacation packages. Scammers prey on the desires of travelers to find affordable deals or exclusive offers, using various tactics to trick them into making payments for non-existent or subpar services. Criminals may operate look-alike websites for airlines, popular travel companies, tourist visa procurement, and federal Trusted Traveler programs like TSA PreCheck to harvest personal data from people who believe they're booking tickets or signing up for smoother airport screening.
Also, bogus insurance brokers sell travel policies they falsely claim will cover pandemic-related cancellations.
"Update Account” Scams. Update account scams are just phishing in which crooks claim an urgent need to update or verify account information for security reasons or system upgrades. The messages often contain links that direct victims to fraudulent websites designed to steal their login credentials, credit card details, or other sensitive information.
Utility Scams. Utility scams involve fraudulent activities targeting individuals or businesses by impersonating utility companies, such as electricity, gas, or water providers. Scammers use various tactics to deceive victims and extract money or sensitive information. They may contact individuals via phone calls, emails, or in-person visits, claiming to represent the utility company, demanding immediate payment for overdue bills, or threatening to disconnect services. They may also pose as utility company representatives offering special discounts, refunds, or upgrades, requesting personal or financial information for verification purposes.
Vacation Scams. Vacation scams involve fraudulent practices targeting individuals looking to book vacations or travel accommodations. Scammers often use enticing offers, deceptive websites, or misleading advertisements to trick victims into paying for non-existent or subpar vacation packages. They may claim to offer exclusive deals, discounted rates, or luxurious accommodations to attract unsuspecting travelers. These scams can involve fake vacation rentals, non-refundable deposits, hidden fees, or misleading information about the location or quality of the accommodations.
VA Pension Poaching. VA pension poaching scams target veterans and their families eligible for VA pensions or other benefits. Scammers, often posing as financial advisors or legal professionals, exploit veterans by offering assistance in obtaining increased pension benefits or promising faster processing times. They may charge excessive fees or convince veterans to transfer their assets into irrevocable trusts or annuities, ultimately leaving them financially vulnerable.
Veterans Charity Scam. American Disabled Veterans Foundation. Healing Heroes Network. Veterans Fighting Breast Cancer. Military Families of America. They sound like just the organizations that generous Americans would rush to support to repay those who have served the country and now need our help.
“Sound like” is the operative phrase here. These are all sham charities that federal and state watchdogs have sued in recent years for misleading donors, according to the Federal Trade Commission (FTC). It’s a particularly shameful subset of charity fraud: scams that exploit Americans’ gratitude for military members’ service and sacrifice. Bogus military charities use the same outreach techniques as trusted nonprofits — direct mail, email, phone calls, texts — and often adopt similar names. They throw around words like “warriors,” “heroes,” and “disabled” and fill their communications with heartrending appeals like this:
Veterans Scams. Veterans scams involve fraudulent activities targeting veterans and their families, taking advantage of their service and the benefits they are entitled to. Scammers employ various tactics to exploit veterans, often posing as government representatives, financial advisors, or veterans' advocates. They may promise increased benefits, faster processing times, or exclusive opportunities in exchange for upfront fees, personal information, or access to financial accounts. These scams include pension poaching, fraudulent employment offers, bogus disability claims, or identity theft.
Weight-Loss Scams. Bogus diet products and programs rank No. 1 among healthcare scams reported to the Federal Trade Commission (FTC), accounting for over a third of such complaints in 2020.
Weight loss scams involve deceptive practices that target individuals seeking to lose weight or improve their physical appearance. These scams often make unrealistic promises of quick and effortless weight loss, using various tactics to exploit people's desires for a fit and healthy body. They may promote miracle pills, fad diets, or "revolutionary" exercise equipment that claim to deliver dramatic results without requiring lifestyle changes or effort. These scams can also include false testimonials, before-and-after photos, or misleading scientific claims to lend credibility to their products or programs.
Who's Who Scams. Who's Who scams, also known as vanity publishing scams, target individuals in professional or academic fields by offering them the opportunity to be included in an exclusive or prestigious directory or publication. Scammers often pose as representatives of reputable organizations and use flattering language to entice victims into paying substantial fees for their inclusion in the publication. However, these publications typically need more genuine prestige or recognition within the industry. Sometimes, the directory may only reach a narrow audience or have a significant value.
Work-From-Home Scams. Work-from-home scams involve fraudulent schemes that target individuals seeking employment opportunities or the flexibility of working remotely. Scammers exploit the desire for remote work by offering enticing job offers that promise high earnings, flexible hours, and the convenience of working from home. However, these scams often require individuals to pay upfront fees for training materials, access to job listings, or specialized equipment. Sometimes, the promised work may not exist, or the tasks assigned may be illegitimate or low-paying.